Let’s imagine we’re kids again, and we’re sitting in the school playground. We have our Pokemon trading cards out, and we decide to trade two cards roughly equivalent in value. There’s nothing particularly tricky about this exchange. We both agree the trade is fair, and I give you my card and you give me yours. Nice and easy.
Being responsible 10-year-olds, we don’t need to ask the teacher to supervise this exchange and make sure the cards are traded correctly. It’s obvious who now physically owns each card, as they’re in our respective decks. I can see them. You can see them. We agree the trade was successful.
That was pretty straightforward. Everyone got what they wanted and no tears were shed. But now let’s imagine what would happen if we were trading digital Pokemon cards.
Let’s say I had the most valuable card in the game—of which there was only one—and I wanted to transfer it to you.

How could you be sure I didn’t make a copy on my computer before sending it to you, thereby making it much less valuable? What if I made 1,000 copies and I sold all of them as if they were the only one?
There would be no way for you to make sure I wasn’t doing this. It would be a bad outcome for you, as well as for the Pokemon trading card community, as once-rare cards become worthless because of oversupply.
Turns out this issue has a name: the double-spending problem. When exchanging digital goods, how do you know somebody hasn’t sent the same asset to two people simultaneously? How can I ensure you haven’t duplicated the digital Pokemon card you want to send me?
We could use a ledger—a record of transactions—to track our trade. Nintendo would have to control this ledger so they could oversee and track every Pokemon trade to make sure nobody is duplicating cards.
This approach has a problem, however. Now that there’s a third party involved in our trade—a middleman, if you will—we’ll always have to go through them to complete our trade.
It’s not just you and me in the schoolyard anymore; we need to put our trust in this third party. We have to trust them not to tamper with the ledger. How can you be certain that the rare card I’m about to give you hasn’t already been duplicated in secret by a Nintendo employee to give to his little brother?
Once again, same outcome. We can’t be 100 percent sure nobody has tampered with the ledger.
But here’s a mind-bending idea: What would happen if, instead of keeping the ledger on one computer at Nintendo HQ, we gave a copy of the ledger to every Pokemon trader?
There are thousands upon thousands of Pokefans around the world, so if everybody kept a copy of the ledger, everybody would be notified when I sent my rare card to you.
And the ledgers would reflect that only one of these cards exists, so if I duplicated it in secret to keep in my account, my copy of the ledger wouldn’t match everyone else’s and it would be rejected. But how would the whole network actually verify that our Pokemon card trade—and, for that matter, all trades—is correct?
Things are about to get complicated, so let’s look at an example. Say there are 1,000 computers participating in this Pokemon trading network—let’s call them nodes.
All these nodes have a copy of the shared ledger, and all are running free software that allows them to talk to other computers on the network. Their purpose is to independently validate every Pokemon trade.
These nodes must agree on what the shared ledger says about transactions that happen on the network. If I make a trade with you, that trade is placed into a temporary unconfirmed transaction pool where it awaits confirmation. Then a bunch of these nodes race to validate all the unconfirmed transactions in a given period (say, 10 minutes).
These nodes are called miners, and they’re racing to be the first to validate this group of transactions—a block—because they could win a stack of Pokemon cards for their efforts. The history of all Pokemon trades is stored as a chain of these blocks (hence blockchain) that makes up our shared ledger.
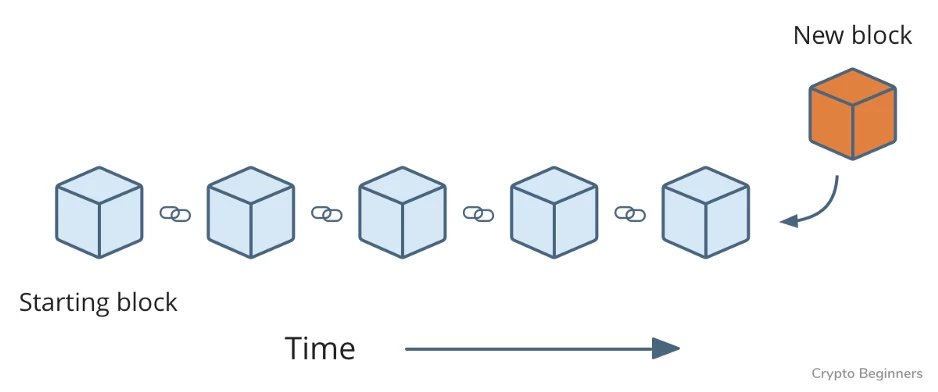
Next, the miners compete to be the first to validate a new block. They do this by expending huge amounts of computing power trying to solve cryptographic puzzles. The network forces these miners to do a lot of hard work to validate each block in order to discourage cheating. You’re less likely to mess with the ledger if it’s expensive to do so.
Once a miner has found the solution to the cryptographic puzzle that validates a block, it signs the block digitally to prove the block is verified and announces this to the network of nodes. The miner then distributes the verified block to everyone else to update their ledgers with the new transactions and collects its prize of Pokemon cards.
However, none of the nodes actually trusts each other, so every time a new block gets passed around, every node checks every transaction in the block against the history of transactions to see if a card has been double spent. This is how the network reaches consensus.
But imagine I was sending you one of my cards in exchange for something in the real world—say, your lunch, because it looks delicious. What happens if I made that trade with you, took your lunch, and then immediately tried to resend the same Pokemon card I just gave to you?
Let’s say send A was to you and send B was the second, illegal double spend. The network doesn’t know whether A or B is the right one, so how does it decide? Both will go into the unconfirmed pool, and they’re generally picked to be put into a block in chronological order, but sometimes not.
Because the blockchain verifies chronologically—i.e., the further back in the chain a transaction is, the more secure it is—if send B is validated first, that’s the true transaction in the eyes of the ledger holders, and A is the double spend.
What should you do in order to avoid being left with no Pokemon cards and no lunch? Your best option is to wait. It’s impossible for the network to accept both spends, so one will always be rejected. It’s just a matter of waiting to see which will be included in the next block.
If you waited at least 10 minutes (sometimes a bit longer), you could verify that the network has accepted send A, that you have your Pokemon card, and that it’s safe to give me your delicious lunch. Everything is right with the world.
Or is it? What would happen if I was extra greedy and didn’t want to play by these rules? What’s stopping me from later going back through the ledger and removing that first send from the record so I can trade the card again and get more lunches?
That trade is stored in a block of information, and blocks are linked linearly in time, so it’s probably buried behind a bunch of blocks by now. If nine newer blocks had been added since my first trade, I could find the 10th block, where my trade is recorded, and delete it.
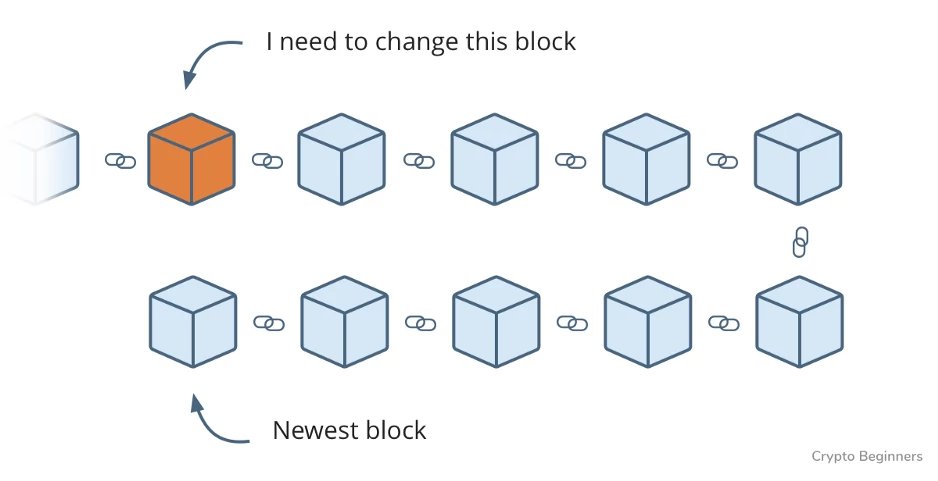
But remember the digital signature that is put on each block? It’s generated based on the information in the block, so changing the data (i.e., removing my trade) automatically changes the signature.
And, to make things worse for me, every signature in every block after this one is also partly determined by the signature before it and will change if the previous signature changes. So I have to fix not only the signature on the 10th block, but also on nine newer blocks in the chain.
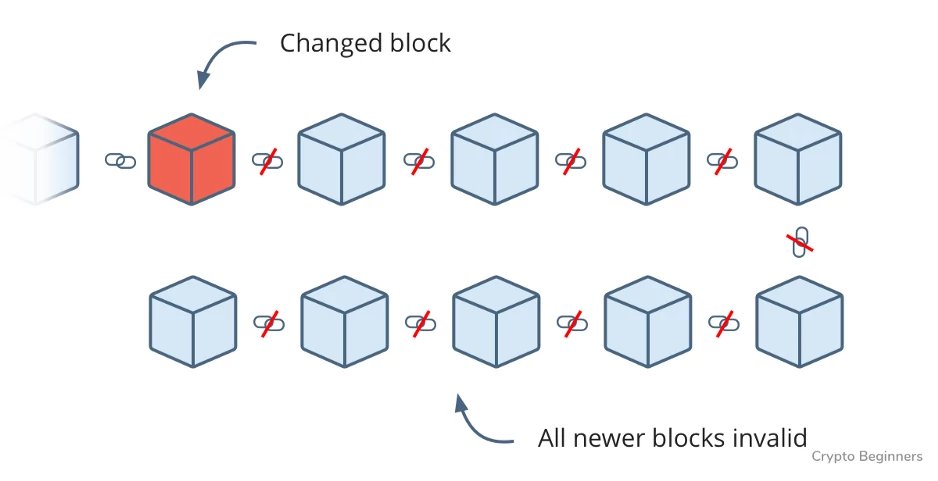
To make matters even worse, I’m doing this only on my copy of the ledger. All other copies are happily agreeing on what already happened. I have to do all of that work on more than 50 percent of the computers in the network to gain the majority consensus.
And to make matters still worse, remember that your computer has to do a lot of hard work to generate those digital signatures. Recalculating the signatures for multiple blocks across the majority of the network would require a staggering amount of power—I’m talking multiple warehouses worth of computers, stacked to the ceiling, running 24/7.
It’s not worth it for me to attempt this because I’d end up way worse off than I started.
And, just like that, we’ve created an open, decentralized, irreversible, tamperproof digital network for trading valuable assets.
This is a simplified version of how bitcoin and blockchain technology works, but it’s easy to see how this tech gives bitcoin its unique and fascinating properties. If you made it this far, I want to give you a high five because you now understand more about bitcoin and blockchain technology than 95 percent of people—just by using Pokemon.